Ransomware- The A-Z You Should Know About One
Ransomware- The A-Z You Should Know About One

According to this survey conducted by Sophos for approximately 5400 organizations, 37% of these companies were hit by ransomware last year.
Consider the Kaseya ransomware attack. This attack was a result of an authentication bypass vulnerability in their VSA web interface. On July 2nd, 2021, the company announced that it had become a victim of a ransomware cyberattack. The attackers had carried out a supply chain cyber-attack. This was accomplished by leveraging a vulnerability in Kaseya’s VSA software against multiple managed service providers (MSP) and their customers, affecting up to 1,500 businesses.
These stats and information show that ransomware attacks are evolving and continue to be on the rise. With the techniques used by cyber attackers getting sophisticated and targeted, it has become important for cyber security specialists to adopt a holistic approach to this cyber threat.
Having said that, let us now look into the details of ransomware.
Contents
| What is Ransomware? |
| How Does Ransomware Work? |
| Ransomware Defense Lifecycle |
| How Can You Avert a Ransomware Attack? |
| How Can You Respond to a Ransomware Attack? |
| Wrap Up |
| About Us |
What is Ransomware?
Ransomware is malware that is used by hackers to hold the victim's (your organization's) critical data at ransom. Here, the sensitive data is encrypted so that you aren't able to access your files, databases, or applications. The hackers further demand a ransom, in turn, to provide you the access.
Ransomware is designed by hackers in a way such that it spreads across a network and encrypts all your data files and servers. This type of cyberattack is threatening because it easily paralyzes your entire system, bringing your complete productivity to a grinding halt. Moreover, such incidents harm your business. Your clients may lose trust in your cybersecurity paradigm, thereby hitting hard on your business.
Also, you may have to churn out billions of dollars to pay these cybercriminals, resulting in significant expenditures and a financial setback for your organization.
How Does Ransomware Work?
Ransomware utilizes asymmetric encryption techniques. This involves cryptography that uses a pair of keys to encrypt and decrypt a particular file or data. The pair of public-private keys are unique for the “attacker-victim”. The pair of private keys are ideally stored on the attacker’s server. It is exposed to the victim only after the demanded ransom has been paid.
There are several variations of malware used in a ransomware attack. It can be through using phishing email campaigns or via targeted spear-phishing attacks. In either case, the malware will need a medium or attack vector to establish contact with the targeted endpoint. Once this has been accomplished, the malware will remain on the system until the task has been completed.
A successful exploit is followed by the ransomware dropping and executing a malicious binary on the targeted system. This binary search and encrypts valuable files, documents, images, and databases. You should also note that the ransomware can spread to other systems, networks across your entire organization.
This is followed by the hacker notifying you to pay a ransom within a stipulated period of time. If you do not have a data backup or if those backups were themselves encrypted or deleted, you may be left with no other option but to pay the ransom to recover your sensitive information.
Ransomware Defense Lifecycle
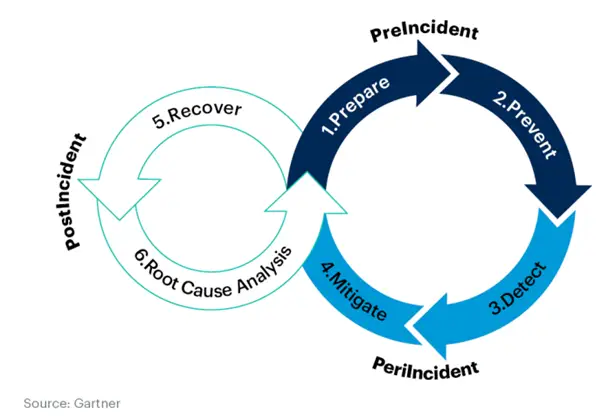
The image above elaborates on the ransomware defense lifecycle. Quantum Strides specializes in preparing and preventing your organization from falling prey to a ransomware attack.
Our cybersecurity services help you create a layered defense strategy in the Prevention and Detection stages thereby helping to leverage intelligence data and the risk scoring obtained from our analysis.
With this idea, let's now look into the ways to prevent a ransomware attack.
How Can You Avert a Ransomware Attack?
To avoid ransomware and mitigate damage, you should consider following these tips:
1. Scan Everything, Patch Everything
Ensure that you scan your systems frequently to identify vulnerabilities that could be leveraged by attackers. Do you have an OT environment? Scan it as well. Ensure that all your systems are timely patched and updated, especially for your security software. Stay on top of updates as patches include remediation for flaws in the software.
2. Securely Back-Up Your Data
Ensure that all your data is backed up, preferably in the cloud or on external repositories. Double-check that the backup is secure and air-gapped from your network. This way, even if your organization is hit by ransomware, you’ll have a safe copy of your data to go back to. Though maintaining backups does not prevent ransomware, it can mitigate risks as a result of one.
3. Educate Your Workforce On Surfing Best Practices
Make sure your workforce is aware of internet surfing best practices. They should be educated to prevent clicking on unknown links, downloading attachments from suspicious sources, and visiting websites that aren’t secure.
4. Avoid Public Networks
Avoid connecting your system on public networks especially when you are working on confidential data. Remote or hybrid workforce? Then, it is best to use a Virtual Private Network (VPN) for stepped-up security.
5. Implement A Security Awareness Program
Conduct cybersecurity awareness programs at regular intervals. This will make sure that your employees are updated. This will also train them to steer clear away from social engineering attacks and phishing attempts. You should also conduct drills or mock tests to check if the information conveyed has been observed.
How Can You Respond to a Ransomware Attack?
The first thing to do if you are hit with a ransomware attack is to respond swiftly. Though there are several ways you can minimize the negative impact of a ransomware attack, here are a few ways you should consider to have your business bounce back to normalcy.
1. Isolate Affected Devices
If just one of your devices in a system has been infected, you should consider disconnecting all the other systems, networks, file sharing connected to that particular device. This will curtail the damage to the device and make it less likely for other devices to be infected too.
2. Control The Spread
Mere isolation of the infected device will not pay off. This may not guarantee the spread of ransomware. To ensure the safety of your network, share drives, and other devices, make sure you disconnect all other devices behaving suspiciously, including those operating off-premises. It is also a good idea to shut down their wireless connectivity for stepped-up security.
3. Assess The Extent Of The Damage
To check for damaged devices, look for files with unusual extensions. Check if any files are creating trouble while accessing. If you find files or devices that haven’t been completely encrypted, isolate them immediately. Check network storage devices, laptops, smartphones, and other possible vectors. Turning off the sharing capabilities can also be prudent.
4. Locate The Entry Point
Tracking the infection will be easier if you identify the source. Check for alerts you may have received from your anti-malware, antivirus, SIEM, or any other monitoring platform. Ransomware usually enters your network through malicious links or emails. Check for such end-user actions. Finally, taking a look at the properties of the files can also provide a clue. The person who has been listed as the owner is probably the entry point.
5. Consider Decryption Options Or Restore Your Backups
No More Ransom provides decryptions for many ransomware types. Alternatively, after completely removing the ransomware from your network, validate that you have an uninfected and complete backup to restore your business from there.
Wrap Up
Similar to other forms of malware, ransomware is a serious type that can prove to be catastrophic to your organization as a whole. Diligent monitoring, appropriate awareness amongst your workforce, and careful action can help mitigate risks.
Are you already working on a strategy for ransomware defense? Feel free to contact us or drop us an email cybersecurity@quantumstrides.com.
About Quantum Strides
Quantum Strides is a connoisseur in a plethora of cybersecurity offerings in the ransomware domain, that include but are not limited to awareness training, phishing simulations, and dark web monitoring for corporate stolen credentials.
Comments
Post a Comment